.png)
Script-based solutions often fall short in meeting PCI DSS 6.4.3 and 11.6.1, especially in preventing tampering with payment pages. These methods have limitations such as dependency on execution order, browser compatibility issues, and inability to block malicious scripts. DataStealth offers a more effective alternative by providing proactive tamper detection without relying on scripts or browsers, ensuring full compatibility and real-time protection. This solution simplifies compliance, reduces IT burden, and better safeguards payment data, offering a more reliable approach to meeting PCI DSS requirements.
When it comes to Payment Card Industry Data Security Standard (PCI DSS) compliance, many businesses turn to script-based solutions as a quick fix. However, while they may seem like an easy answer, script-based solutions often fall short—especially when it comes to more complex requirements like PCI DSS 6.4.3 and 11.6.1. These requirements are even more important to pay attention to for organizations processing high volumes of transactions because even if a breach lasts a single day, that could mean hundreds of thousands of stolen payment cards.


The most recent version of PCI DSS (4.0.1) introduces two critical new requirements, 6.4.3 and 11.6.1. These two requirements address vulnerabilities within online payment pages. Many organizations are just learning about these new requirements during their PCI Compliance audit and are struggling to find an adequate solution that not only alerts but effectively blocks malicious or unauthorized content.
The consequences of not implementing a solution before the April 1st, 2025 deadline are significant. Fines can reach up to $100,000 monthly, while the financial and reputational impact of a data breach can be devastating, averaging $4.88 million per incident in 2024 based on the most recent IBM Data Breach Report. Beyond these penalties, companies risk losing their ability to process card payments entirely, resulting in even more catastrophic financial losses and major disruptions to their business operations.
PCI DSS requirements 6.4.3 and 11.6.1 call for a proactive approach by implementing continuous monitoring and stringent controls to detect and prevent tampering or unauthorized changes in real-time.
Requirement 6.4.3 requires organizations to create an inventory of all scripts delivered to the user through the payment page, provide written justification as to why each script is being used, and ensure that no scripts have been tampered with.
Requirement 11.6.1 requires a mechanism that will alert on any unauthorized change to HTTP headers and script contents of payment pages as received by consumer’s browsers.
Many organizations have turned to script-based solutions to meet these requirements; however, these scripts intended to monitor all other scripts can be blocked or disabled themselves. Here’s why businesses must rethink their reliance on scripts and consider more robust solutions.
The growing sophistication of browser-based attacks exposes critical gaps in script-based solutions, often failing to detect when attackers are covertly harvesting cardholder data. Client-side threats, like e-commerce skimming and injections (commonly used by Magecart), exploit these limitations by embedding malicious code directly into the browser, bypassing traditional server monitoring and leaving sensitive data vulnerable at checkout before it even reaches the server.
These browser-level attacks are rampant. Mastercard reports that nearly 75% of publicly disclosed data breaches in 2022 were attributed to digital skimming. Cybercriminals compromised 4,500 new websites that year, marking a staggering 129% increase compared to 2021. The trend worsened in 2023, with another 2,700 sites targeted. These breaches resulted in millions of dollars in losses and triggered significant regulatory penalties. For instance, British Airways was hit by a Magecart attack that exposed 380,000 card details in just 15 days, resulting in a $230 million fine. Such incidents underscore the urgent need for proactive, client-side monitoring rather than reactive, script-based methods to safeguard payment data and meet compliance requirements effectively.
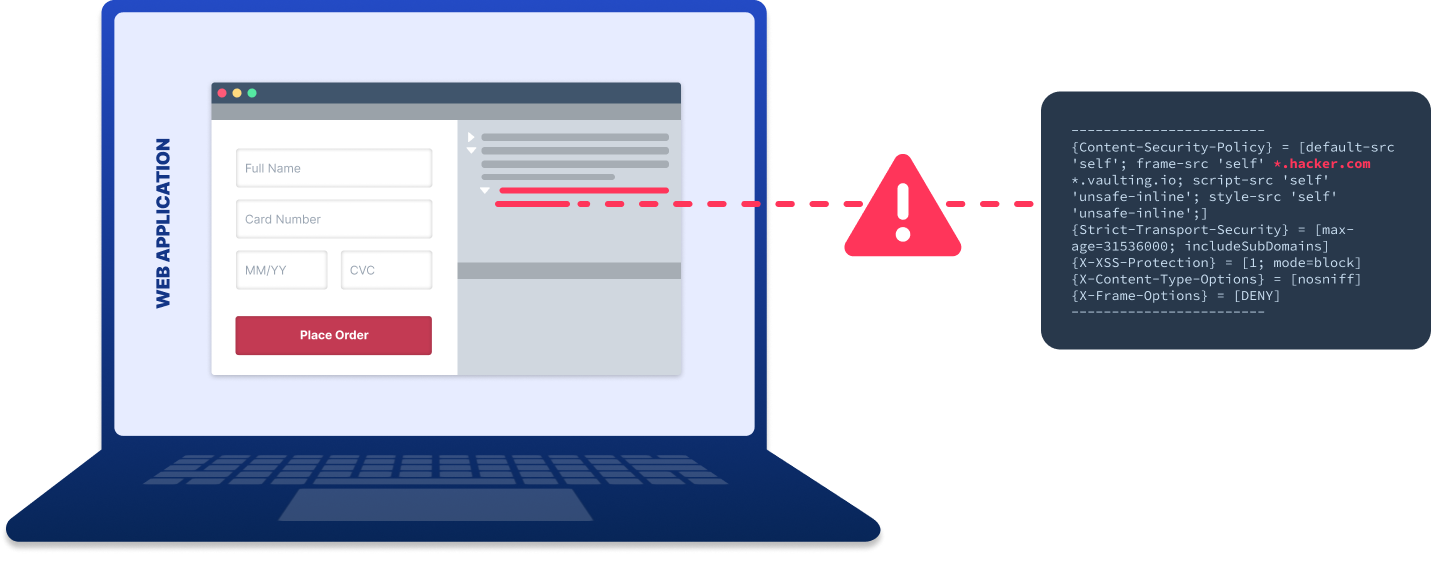

DataStealth’s Tamper Detection and Protection solution was purpose-built to address PCI DSS v4.0 requirements 6.4.3 and 11.6.1. Its patented technology is unique because it does not require any code changes or installation of additional scripts, agents, or collectors. It enables organizations to maintain compliance without relying on untrusted browsers or reactive scripts by monitoring and validating content before it reaches the consumer. Key advantages include:
The transition to PCI DSS v4.0 represents a significant organizational shift, requiring more dynamic and thorough security measures. For organizations struggling with requirements 6.4.3 and 11.6.1, DataStealth provides an efficient, scalable, and proactive approach by providing organizations with compliance autonomy, making it easier to achieve and sustain PCI DSS compliance while protecting customer data effectively. By choosing a purpose-built solution like DataStealth, organizations can meet their compliance obligations and reduce risks, optimize IT resources, and foster greater customer trust.