Enforce least-privilege access in any application with attribute-based, in-flight masking – no code changes, no agents, no disruption.

Walls stop outsiders. Over-privileged insiders and third parties still see too much. Broad access to sensitive fields creates avoidable exposure and compliance headaches.

Static roles expose entire records when users only need specific fields.
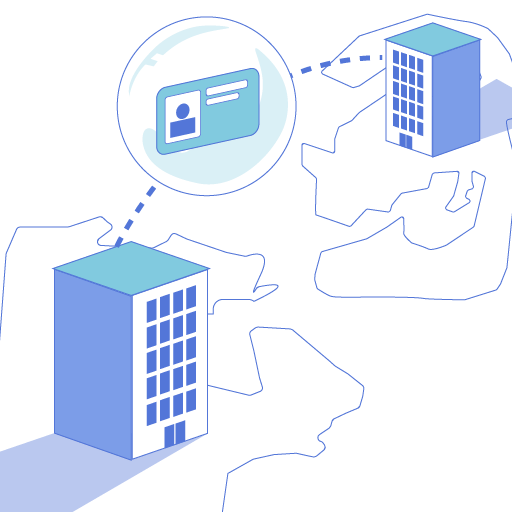
Offshore support, contractors, and even admins retain standing access to PII.

Custom logic per app is slow, fragile, and impossible to keep consistent across your estate.
DataStealth Dynamic Data Masking enforces least privilege in real time. Users see exactly what they need – and nothing more.

Go beyond roles: evaluate user, device, location, time, risk from your IdP (e.g., Entra ID) to decide field/row-level visibility on each request.
We never alter source data. Masks apply in-flight (redact, partial reveal, generalize) at the moment of access – Zero Trust at the data layer.
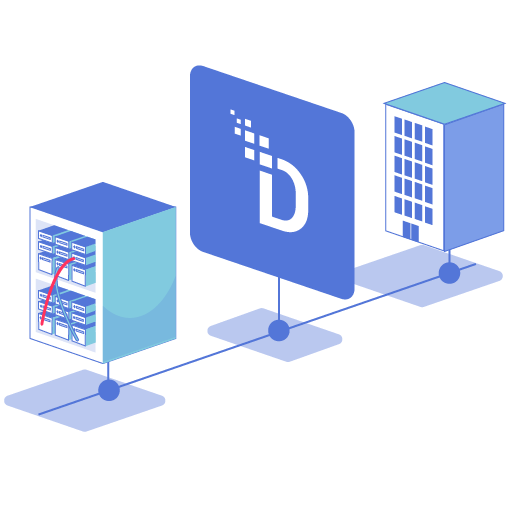
Define and enforce consistent masking policies across cloud, on-prem, and legacy from one console – no application code changes.

Agentless, network-layer insertion transparently inspects outbound responses – no code, no plug-ins.

On each request, we query your IdP and context (role, group, geo, device posture, time, risk) to compute precise entitlements.

Policy determines the view: **redact a column, mask a row, partial reveal (e.g., **1234), or full access. Source data remains unchanged.

Get expert answers on how to deploy DataStealth at enterprise scale in your environment without performance trade-offs, code rewrites, or disruption.
SCHEDULE A CALL