Enforce residency, eliminate third-party exposure, and stay compliant, without changing a line of code.
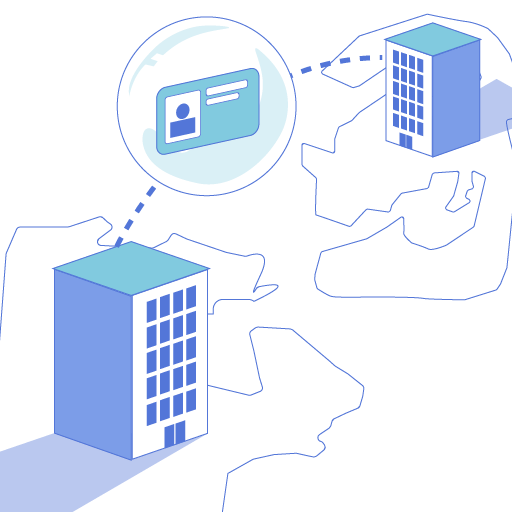
The result: global SaaS adoption and cross-border workflows with zero risk of violating data residency or exposing PII.
Every SaaS app, GenAI service, API call, or offshore team is a cross-border data transfer you don’t fully control. Each one increases your exposure to breaches, leaks, and non-compliance.
DataStealth was built for this reality.

Adopt any SaaS platform with confidence. We tokenize sensitive data in-flight, so vendors only ever process valueless tokens, not customer PII.

Guarantee that regulated data never leaves its jurisdiction. Our gateway neutralizes data before it crosses the border, ensuring compliance with GDPR, PIPEDA, HIPAA, and more.

Offshore and remote teams get the access they need, while dynamic masking ensures only the right people see real data, based on role, location, and context.
DataStealth operates transparently at the network layer, giving you total command of cross-border data flows without slowing down business.
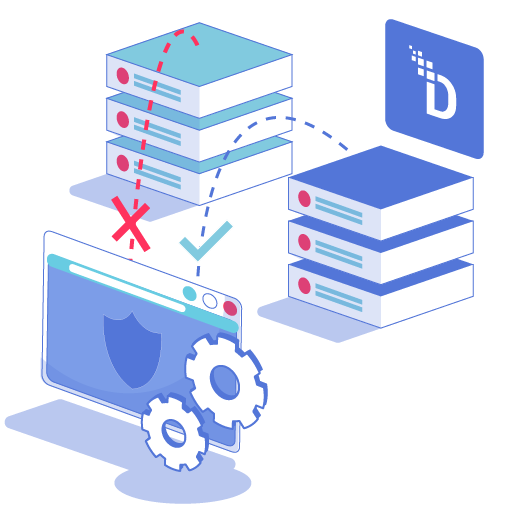
Protect any data flow with a simple network change. No agents to manage, no code to modify.
Apply granular rules to every flow: tokenize PII headed to cloud, mask it for offshore teams, or grant full access to local admins – all from one console.

Neutralize sensitive data before it crosses any trust boundary, creating a provable, continuously enforced compliance posture.

A Canadian insurer was blocked from using U.S.-hosted Salesforce Marketing Cloud due to strict residency laws forbidding PII from leaving Canada.

DataStealth deployed in-line, intercepting all Canadian PII and replacing it with format-preserving tokens before it reached Salesforce’s U.S. servers.

The insurer launched Salesforce with full functionality, zero disruption, and 100% compliance, turning a residency barrier into a growth enabler.
Purpose-built for high-volume enterprise environments, DataStealth applies consistent, scalable protection across cloud, SaaS, and legacy systems.

Replace sensitive values with format-preserving tokens that have no mathematical link to the original data.

Hide or redact data dynamically based on user role, location, or IP, enforcing true least-privilege access.

Provision anonymized, high-fidelity test data for dev and QA teams worldwide, structurally consistent, but free of real PII..
Get expert answers on how to deploy DataStealth at enterprise scale in your environment without performance trade-offs, code rewrites, or disruption.
SCHEDULE A CALL