DataStealth’s automatically discovers every data source – structured and unstructured – including forgotten dev copies and shadow IT. Then it scans 100% of the data with advanced validation to deliver a trustworthy inventory with near-zero false positives.

A defensible security program starts with a complete data inventory. Yet most discovery tools were built for yesterday’s estates – not today’s sprawl of databases, file shares, SaaS, and shadow IT. The result: blind spots, wasted effort, and regulatory exposure.
The production database isn’t your biggest risk. It’s the forgotten dev copy or the shadow IT share no one tracks. Tools that need predefined targets will always miss what matters most.
For GDPR, PCI DSS 4.0, and CCPA, “mostly” isn’t good enough. Sampling can’t deliver the cell-by-cell accuracy needed for compliance or “right to be forgotten” requests.


Regex-only scanners bury teams in noise. Chasing false positives wastes hours and creates alert fatigue – the perfect recipe for missing the real threat.
DataStealth’s discovery engine was built for scale, precision, and modern hybrid estates. It finds and classifies sensitive data everywhere – structured and unstructured – with accuracy you can defend to regulators and the board.

Point our agentless scanner at a segment, and it auto-discovers every database, file share, and SaaS connection – even shadow IT your CMDB missed.

Beyond regex: contextual analysis, validation (e.g., Luhn checks, Soundex), and tunable confidence scoring classify with surgical precision.

No sampling. Proven to scan 12B+ rows and 78K tables in production databases, plus unstructured stores, delivering a full inventory for governance and remediation.

A telco needed a complete inventory of sensitive data across massive databases – including 12B rows, 78K tables – plus sprawling file shares.

DataStealth scanned both structured and unstructured sources at full scale, accurately identifying PII and mapping concentration with cardinality analysis.

The company gained a defensible, board-ready inventory and prioritized protection based on real-world risk instead of guesswork.
By scanning 100% of flows and stores, DataStealth builds a trusted, actionable inventory of PII, PHI, and PCI across your estate. At the same time, sensitive values can be tokenized at the source, ensuring that at-rest data is neutralized and useless to attackers.
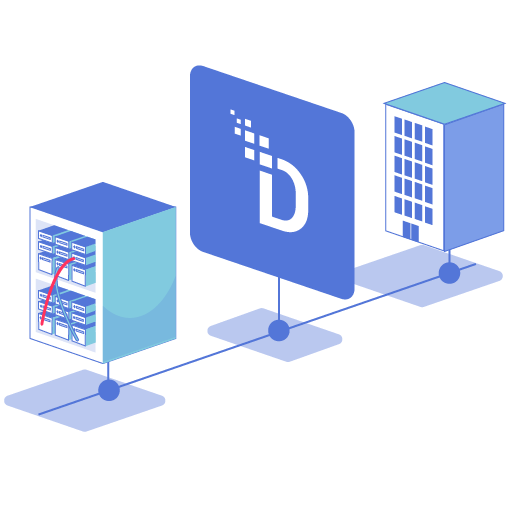
Sitting inline at the network layer, DataStealth inspects traffic across HTTP, SFTP, JDBC, ODBC, and more. It automatically discovers structured and unstructured data sources – including shadow IT and forgotten dev copies – without agents or code changes.

Our engine applies contextual analysis and advanced validation (e.g., Luhn checks for PANs, Soundex for names, regex + heuristics) to classify data in real time with near-zero false positives. Every sensitive element is tagged with type, confidence, and location for complete accuracy.