DataStealth deploys directly inside your data center – on bare metal, VMs, containers, or Kubernetes – so sensitive information never leaves your trust boundary.
From regulated workloads to tightly controlled or even air-gapped environments, you maintain full control without sacrificing protection.

Tokenize or mask fields in real-time by placing DataStealth between apps, users, or services – no code changes required.
Enforce field-level protection on SQL or NoSQL traffic without modifying your database engine.

Run DataStealth alongside microservices to enforce per-service policies with minimal development effort.
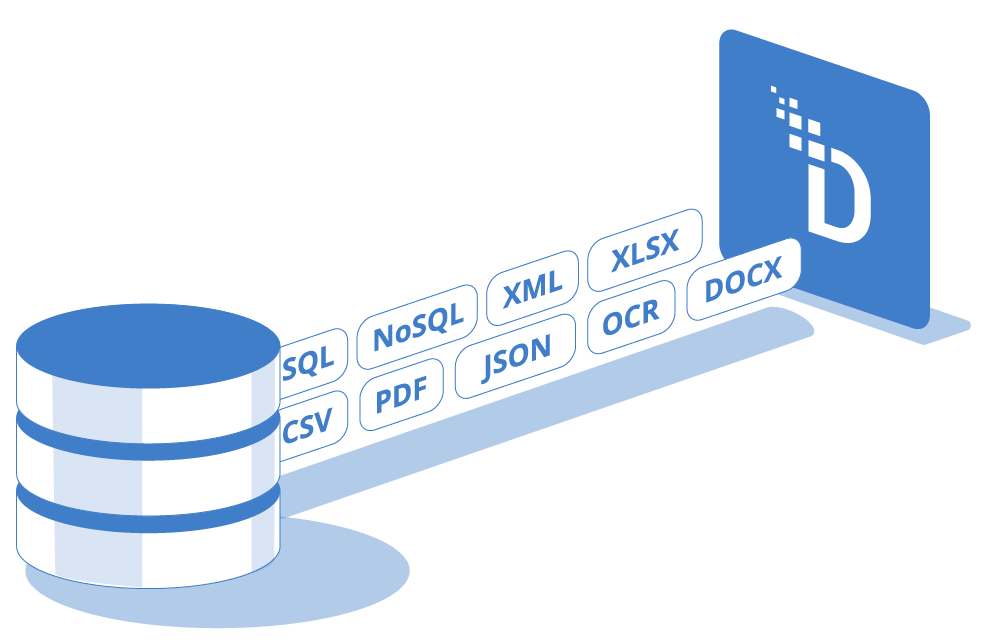
Discover, classify, and protect sensitive data at scale across files, data lakes, and event streams.


Active-active nodes behind your load balancers keep protection continuous – even in restricted or air-gapped deployments.
Horizontally scale brokers and workers across bare metal, VMs, or Kubernetes to meet any throughput or latency target.

Policies are managed as code with versioning, approvals, and rollbacks – so enforcement is consistent and error-free.

Every action is logged and exportable to your SIEM, giving you complete traceability and real-time compliance reporting.
Protect HTTP(S), gRPC, and GraphQL through gateways or service meshes.
Apply field-level tokenization/masking across SQL and JSON.
Secure CIFS, NFS, and S3-compatible targets.
Integrate with Kafka, queues, and ETL pipelines.
Automatically scrub sensitive data before it hits logs, tickets, or traces.

See how DataStealth deploys in your data center, secures legacy and modern systems alike, and enforces protection at scale – all without adding complexity or slowing down your teams.