DataStealth neutralizes sensitive data at the source and replaces it with secure, format-preserving tokens that hold no exploitable value. Even if attackers break in, there’s nothing worth stealing.


Databases and file shares are prime targets. At-rest encryption only buys time – stolen ciphertext today could be decrypted tomorrow.
TLS protects the pipe, not the payload. Once data lands in a SaaS app, partner system, or microservice, it’s in the clear.

Juggling point tools for databases, file shares, and flows leaves gaps everywhere. Hybrid estates demand unified protection, not fragmented patches.
DataStealth isn’t another layer. It’s a data-centric architecture that renders sensitive data worthless before it becomes a liability.

Replace live PII/PHI/PCI with valueless, format-preserving tokens. Unlike encryption, tokenization is non-mathematical and keyless, inherently resistant to brute force and future threats.
Safeguard data in any app, database, or file store – including legacy/mainframe – without touching source code or breaking schemas.
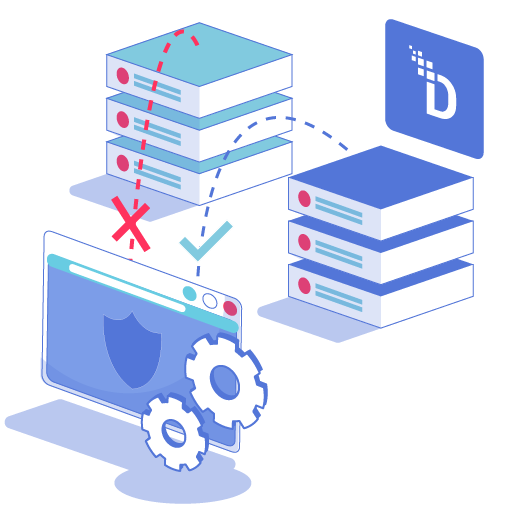

Apply one consistent control for data in motion and at rest across on-prem, multi-cloud, and legacy. Prove PCI and privacy compliance by design.

A leading insurer needed a U.S. SaaS platform but refused to let customer PII leave its jurisdiction.

DataStealth tokenized all sensitive data in-line before it reached the vendor. The SaaS ran normally, processing tokens, not real PII.

Best-in-class SaaS, zero exposure risk. Auditors confirmed no PII was ever at rest with the vendor – compliance assured, breach liability eliminated.
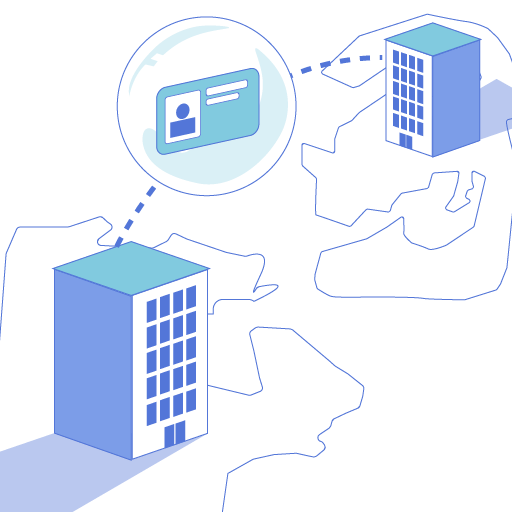
Intercept HTTP, SFTP, and database flows and protect sensitive fields before they leave your control.
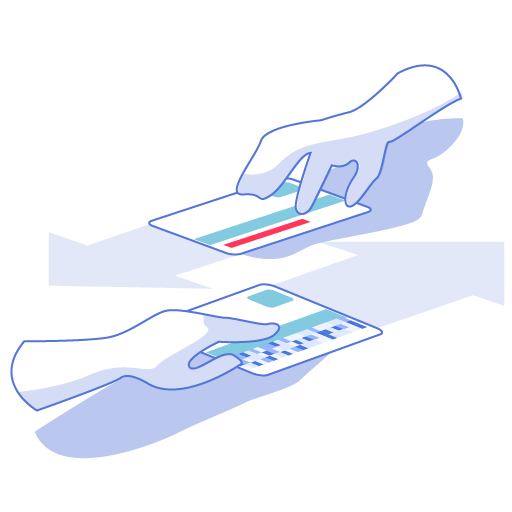
Identify PII/PHI/PCI in real time and replace with format-preserving tokens – applications continue to function.

Apps and databases store/process tokens only. Even a full system compromise yields nothing useful.

Get expert answers on deploying DataStealth at enterprise scale, without performance trade-offs or rewrites.
SCHEDULE My Session